Dangerous WordPress Malware :
A spammer or hacker always try to hack WordPress website or raw PHP website, it's not only those two type website. It could be any type of website. Because a hacker always tries to attack week point into the website. So who developer developed this website and unfortunate keep the security whole into the website it will help for hacker and it could be hacked by the hacker and they could put some malware into this website. The hacker put some shell and try to upload more file like some PHP or python script to execute root permission or brute force to hack cpanel but a hacker anything can do with cpanel if they had successfully uploaded PHP, python, XML shell. Few servers do not accept those file for security reason. But some server accept easily when they can identify the website have some malware then they will generate an email that this server has some malware please take action otherwise your plane will suspend. The message was look like that. some website owner are not check their message continue. That's why they don't know what was problem and they can see only, already hosting plane suspended.They want to contact with hosting provider they are throw a offer that if you want to remove malware you have to pay 300 USD per year.But i am remove the malware from your website only for 20 dollar for each website.
First Step:
If you have malware on the site, you need to backup the site before removing the malware. There are 2 ways to get backup to the WordPress site. The first one is manually backup from Cpanel and the second one is through the plugin.
Manually Backup
- Go to ----> cpanel -> public_html -> (wp content, htaccess & wp-config file zip) These 3 files need to be zipped and downloaded.
Open the ----> wp-config file and search there DB_NAME. Copy this database name and goto phpmyadmin.
You will find the option to switch from cPanel to PhpMyAdmin.
Then In the phpmyadmin Panel, search by database name. See there my database name was “wordpress”. Now I am searching for my database name and click to export database.
Click to go and download the database
Manually backup is complete. You will backup your wordpress site through (updraftplus & all in one wp migration) this plugin. It’s simple, just active one plugin and click to backup site.
Second Step:
Goto Cpanel ----> All files should be deleted except these 3 files (wp config, htaccess and wp content). Then download the WordPress Fresh file from here (https://wordpress.org/download/) and replace the files that have been deleted from cPanel.This means that you can upload all files to cPanel, Exclude the (wp config, htaccess and wp content) this file from your downloaded fresh file.
3rd step:
Reinstall Plugins : Reinstall all your plugins from the WordPress repository or fresh downloads from the premium plugin developer.
Reinstall Themes : Reinstall your theme from a fresh download. Do not upload your old theme, as you may not recognize which files have been hacked.
4th Step:
Activate wordfence plugin and scan your website. If your site is hacked, wordfence will show you many malware files.
See this screenshot. There are Filename: wp-content\themes\astra\index.php. Now It needs to clean the malware script for this location.
This way we have to remove the malware from every file. When the removal of malware from all files is finished then it will be scanned again with wordfence. Hope you understand.
Final & Advanced Step:
Many times malware files on wordfence do not show scan results. In this case you have to go to cPanel. Each file should be monitored. There are 2 ways to detect malware files. You will see the modified date of each file. Some malware files will have filenames with unknown names.And some malware scripts may contain the theme and plugin's index file.You have to manually check every file. Open the file that you suspect and search by eval. If eval word is stay your file that means this file is infected with malware. See those screenshots.
Now remove the malware code. When removal is done then you check the status of your website. Sucuri Site Scan
This screenshot is malware website.
This screenshot is without malware.
DONE. Have A Good Day.
=============================================
Remove Dangerous WordPress Malware from Your Website
HTML and CSS Injection :
Today i will talk about HTML and CSS injection. Any web application design by HTML, CSS and JavaScript, those are executed in client server. So if any attacker try with execute html or CSS or JavaScript code using URL parameter or input field and if successfully execute in client server via remote server. So this web application is vulnerable.
Now i will Demonstrate with PureVPN Official Website, That contain have HTML and CSS Injection. So Lets Start
Today i will talk about HTML and CSS injection. Any web application design by HTML, CSS and JavaScript, those are executed in client server. So if any attacker try with execute html or CSS or JavaScript code using URL parameter or input field and if successfully execute in client server via remote server. So this web application is vulnerable.
Now i will Demonstrate with PureVPN Official Website, That contain have HTML and CSS Injection. So Lets Start
1st Step : Go to the PureVPN Vulnerable website url
2nd Step : Now i am going to find out URL parameter and set my plain text and hit my enter button.
Now we can see the value that content i was set into URL parameter. So Now we can see plain text so we can call it text injection. Ok now we can try with execute html code into this URL Parameter if it will execute this application is vulnerable. So now the HTML code is also executed
Now I am going try with CSS code it will also execute in this URL.
Video POC
HTML and CSS Injection POC for PureVPN
What is Malware ?
Malware is just like a script or unusual tools. It's always harm your website or server and your device. It used for thief your Data or information and money. It's continue made by some Black Hat Hacker to earn money to Black way or Intentionally on someone. but i would like discuss about malware but it's adware but it auto generate from the Malware in web server.
I am Shamim. I am working with cyber security in cyber world. I have an account Fiverr and Upwork I have been solved lot's of web server malware problem. But I am recently face an unique malware issue for Hostgator server. The server has continue generate some adware code into JavaScript and PHP file. That's way your server all of website redirected into a spam and malware website.
Redirected website Below
How to worked ?
The malware load into index.php file using header file by Javascript CharCode. The code continue generate as randomly CharCode. Also the link create infinity loop. When any one load the JavaScript file it will create an set cookie and set cookie value is randomly added.
How to Solved ?
- Please check all of Javascript file and removed all of the Malware code.


- Check all header.php file or Header file and you have to removed malware link according to image below

How to Remove malware from Wordpress || deloq.site, tityx.com and bacic.pro Malware
How To Do Brute Force Attack || Cyber Security Blog
A brute-force attack consists of an attacker trying many word list or Many latter Combination with the hope of Luckily guessing correctly.
The attacker systematically checks all possible Word lists and latter Combination until the correct one is found. Alternatively,
the attacker can attempt to guess the key which is typically created from the password using a key derivation function.
This is known as an exhaustive key search.
1. First we have visit Target website
2. Then we have to open Burp Suite and setting proxy setting in Mozilla Firefox or Any Browser.
3. Then we have to setup Proxy in Burp Suite as a Intercept on.
4. We have try to login in our target website.
5. Then Proxy HTTP History and click right button on your mouse and sent Intruder
6. And Now go to Intruder Option
select Positions
7. Then clean all Variable and select only those things or target variable which u want to brute force
8. and Select Cluster Bomb
9. Then Select Payload and and now you can add all possible words.IF you already know about username then select only one username. if you don't know your target user's username, u can set all possible words List.
Then set password from all possible words list.
Only for username in tab no 1
same. for password list which i have already completed
You can add words by type on burp suite or u can make a word list in txt file.and select it.
Now select any object. The object will be " when u want to login in your target website by typing any user and it will generate error massage if your user info is wrong then error massage make copy and add payload processing
afar all configuration we have click start attack
A brute-force attack consists of an attacker trying many word list or Many latter Combination with the hope of Luckily guessing correctly.
The attacker systematically checks all possible Word lists and latter Combination until the correct one is found. Alternatively,
the attacker can attempt to guess the key which is typically created from the password using a key derivation function.
This is known as an exhaustive key search.
Brute Force Tools :
Burp Suite
And Custom Word List
1. First we have visit Target website
2. Then we have to open Burp Suite and setting proxy setting in Mozilla Firefox or Any Browser.
3. Then we have to setup Proxy in Burp Suite as a Intercept on.
4. We have try to login in our target website.
5. Then Proxy HTTP History and click right button on your mouse and sent Intruder
6. And Now go to Intruder Option
select Positions
7. Then clean all Variable and select only those things or target variable which u want to brute force
8. and Select Cluster Bomb
9. Then Select Payload and and now you can add all possible words.IF you already know about username then select only one username. if you don't know your target user's username, u can set all possible words List.
Then set password from all possible words list.
Only for username in tab no 1
same. for password list which i have already completed
You can add words by type on burp suite or u can make a word list in txt file.and select it.
Now select any object. The object will be " when u want to login in your target website by typing any user and it will generate error massage if your user info is wrong then error massage make copy and add payload processing
afar all configuration we have click start attack
How To Do Brute Force Attack || Cyber Security Blog
Today I want to talk about Two-Factor Authentication Code problem.
Two Factor Authentication is better security for any web Application and this Logic using maximum Web Application.
This security system using that if any hacker got the password from any Facebook account or Web Applications they can not get access their phone number easily. That why it called batter security.But if you try to use Two Factor Authentication code in second time to login to Facebook account it should work successfully unlimited time in Three minutes.I tried and it worked you can see below on video, How to it worked. But Facebook said it's not a bug.
Two-Factor Authentication Code To Login 2nd Time in Facebook users Account || Cyber Security Tech Blog
Today I will discuss Cracking password. The password is the common thing to secure your virtual world like intranet accounts mobile pc or any other devices. Anyone can crack any password. But it has some condition like it maybe takes too big time or few. It depends on Password cracking Algorithm or sometimes you can crack easily in few minutes if you make special word-list for individual password crack and if your luck with you.
Every Cyber Security specialist suggest that use the strong password to keep safe online or any account. But if a hacker gets your encrypted password it's should be cracked.But it's one kind of suggestion not decision. because if you make strong password it will so hard to crack your password but still cracked able this password.
Here is one another thing to get password easily if a user uses common password in everywhere with the same password.
How to find this password?
First of all, I want to say this trick will work well or maybe not worked well.But you can try.Suppose you want to get access any victim account this account should be anywhere. Just collect some information about your victim, like email, name or How much info you have collected.Then search in google and found Where is the place the victim did create account and you can try get access any vulnerable website with the database.If you got success, you should get the user password and now you can try to login with which account get to access using this password.The maximum user uses one password in everywhere.so While it will work well if the user uses one password in everywhere.
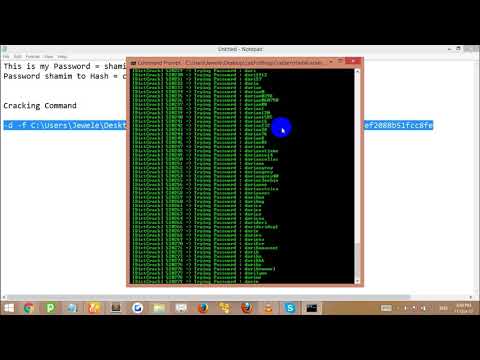
Now I want to discuss Cracked MD5 or SHA-1 Hashes
How to Crack MD5 or SHA-1 Hashes?
1. Download the The Cracker
2. Extract The ZIP file.
3. Copy cmd.exe from Default windows installation drive it's should be C: drive.
How to cracked Password || Easiest Way || Cyber Security Blog
Subscribe to:
Comments (Atom)