How To Do Brute Force Attack || Cyber Security Blog
A brute-force attack consists of an attacker trying many word list or Many latter Combination with the hope of Luckily guessing correctly.
The attacker systematically checks all possible Word lists and latter Combination until the correct one is found. Alternatively,
the attacker can attempt to guess the key which is typically created from the password using a key derivation function.
This is known as an exhaustive key search.
1. First we have visit Target website
2. Then we have to open Burp Suite and setting proxy setting in Mozilla Firefox or Any Browser.
3. Then we have to setup Proxy in Burp Suite as a Intercept on.
4. We have try to login in our target website.
5. Then Proxy HTTP History and click right button on your mouse and sent Intruder
6. And Now go to Intruder Option
select Positions
7. Then clean all Variable and select only those things or target variable which u want to brute force
8. and Select Cluster Bomb
9. Then Select Payload and and now you can add all possible words.IF you already know about username then select only one username. if you don't know your target user's username, u can set all possible words List.
Then set password from all possible words list.
Only for username in tab no 1
same. for password list which i have already completed
You can add words by type on burp suite or u can make a word list in txt file.and select it.
Now select any object. The object will be " when u want to login in your target website by typing any user and it will generate error massage if your user info is wrong then error massage make copy and add payload processing
afar all configuration we have click start attack
A brute-force attack consists of an attacker trying many word list or Many latter Combination with the hope of Luckily guessing correctly.
The attacker systematically checks all possible Word lists and latter Combination until the correct one is found. Alternatively,
the attacker can attempt to guess the key which is typically created from the password using a key derivation function.
This is known as an exhaustive key search.
Brute Force Tools :
Burp Suite
And Custom Word List
1. First we have visit Target website
2. Then we have to open Burp Suite and setting proxy setting in Mozilla Firefox or Any Browser.
3. Then we have to setup Proxy in Burp Suite as a Intercept on.
4. We have try to login in our target website.
5. Then Proxy HTTP History and click right button on your mouse and sent Intruder
6. And Now go to Intruder Option
select Positions
7. Then clean all Variable and select only those things or target variable which u want to brute force
8. and Select Cluster Bomb
9. Then Select Payload and and now you can add all possible words.IF you already know about username then select only one username. if you don't know your target user's username, u can set all possible words List.
Then set password from all possible words list.
Only for username in tab no 1
same. for password list which i have already completed
You can add words by type on burp suite or u can make a word list in txt file.and select it.
Now select any object. The object will be " when u want to login in your target website by typing any user and it will generate error massage if your user info is wrong then error massage make copy and add payload processing
afar all configuration we have click start attack
How To Do Brute Force Attack || Cyber Security Blog
Today I want to talk about Two-Factor Authentication Code problem.
Two Factor Authentication is better security for any web Application and this Logic using maximum Web Application.
This security system using that if any hacker got the password from any Facebook account or Web Applications they can not get access their phone number easily. That why it called batter security.But if you try to use Two Factor Authentication code in second time to login to Facebook account it should work successfully unlimited time in Three minutes.I tried and it worked you can see below on video, How to it worked. But Facebook said it's not a bug.
Two-Factor Authentication Code To Login 2nd Time in Facebook users Account || Cyber Security Tech Blog
Today I will discuss Cracking password. The password is the common thing to secure your virtual world like intranet accounts mobile pc or any other devices. Anyone can crack any password. But it has some condition like it maybe takes too big time or few. It depends on Password cracking Algorithm or sometimes you can crack easily in few minutes if you make special word-list for individual password crack and if your luck with you.
Every Cyber Security specialist suggest that use the strong password to keep safe online or any account. But if a hacker gets your encrypted password it's should be cracked.But it's one kind of suggestion not decision. because if you make strong password it will so hard to crack your password but still cracked able this password.
Here is one another thing to get password easily if a user uses common password in everywhere with the same password.
How to find this password?
First of all, I want to say this trick will work well or maybe not worked well.But you can try.Suppose you want to get access any victim account this account should be anywhere. Just collect some information about your victim, like email, name or How much info you have collected.Then search in google and found Where is the place the victim did create account and you can try get access any vulnerable website with the database.If you got success, you should get the user password and now you can try to login with which account get to access using this password.The maximum user uses one password in everywhere.so While it will work well if the user uses one password in everywhere.
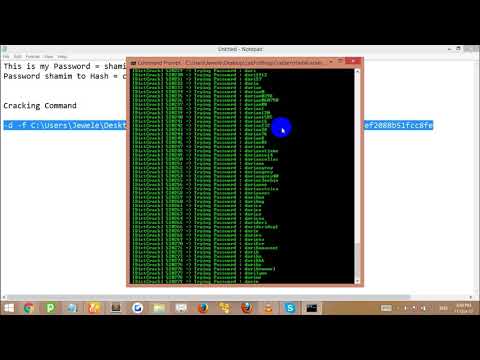
Now I want to discuss Cracked MD5 or SHA-1 Hashes
How to Crack MD5 or SHA-1 Hashes?
1. Download the The Cracker
2. Extract The ZIP file.
3. Copy cmd.exe from Default windows installation drive it's should be C: drive.
How to cracked Password || Easiest Way || Cyber Security Blog
Educational Purpose Only
To day i will discuss about email. All internet user always given first priority to email and in future it's will same position. Every internet user have email. But someone use gmail,yahoo, mail, Microsoft email or they can use private email server with own domain.
What is email ?
Email is someone sent you to something and you will received that means it called information shearing. Virtual things Give and Take.
But now maximum user use email for anywhere to create account and need to maintenance by the email. So every user email need to security from hacker.
How to secure your Email ?
Firstly please keep in your mind Cyber world is not secure. You have to make believed it. Any time can occurs anything. No one give you guaranty that online is secure.
- Keep Strong Password and
- Change your password after few days
- Don't use common password
- Don not use email password in any where
- keep on your Second step verification.
Always check where from you are login your email account (Gmail) and if seen number of device with you have connect so make sure those device is it your's or not. if not remote logout from this.
Why you have to use different password in different website to Make sure your Secures ?
Suppose you are using gmail. Gmail have much security. If anyone want to crack your password it's not easy, so difficult. But if you use this email information in create account in anywhere like buy sell product or alluring website or any where.
So when you create your account using any information it's always saved in there database
so now think about it.
No one easily hack gmail account but if you use your gmail info with password to create an account in unsecured website which website any one can hacked. Easily your gmail account got hacked. So carefully use your information to create any profile in any website.
How to Avoid Scam or unwanted email or How to understand About SCAM Email or Spoofed Mail .
Disclose your email row data and find which server from this email come from.
Please the Image and follow it .
How to Make sure our security from any email come to you || Cyber Security and Web Consultancy
- Run the Windows operating system that you want to use
- Go to Windows Button then search Run and then type %windir%, and then click OK.
Or
- Yo can go with My Computer then click your windows installation Folder (Default C: drive).
- Remember This folder will open.(This folder is Working windows folder).Don't try to delete or remove or rename.
- Find the Windows old folder and remove or delete it and click yes to confirm.
- Now Right click on My Computer or Computer then click Properties.
- Now select Advance tab with Startup and Recovery then click setting then it will show The Startup and Recovery dialog box

- Under System startup, click Edit to modify the Boot.ini file.
The Boot.ini file opens in Notepad and looks similar to the following:
- Click on file in notpade and click save as then backup copy of the boot.ini that name as boot.old.Then exit to close it.
In the [boot loader] section of the Boot.ini file, identify and then delete the line of text for the Windows operating system that you want to remove. For example, if the Windows folder that you removed in step 4 was for the Microsoft Windows XP Home Edition operating system, remove the following line of text from the Boot.ini file:
- click the file in notpade and save it as boot.ini file.then exit it.
- Click OK to close the Startup and Recovery dialog box.
- Restart your computer.
Source : Microsoft
How to remove second installation file or Multiple Operating System
By Firewal Ami
To create a bootable USB drive manually we will use Command Promote windows default Program.Here are step by step to create a boot able USB drive as the windows installation media,We require minimum 4 GB for Manually capacity.If you have . larger capacity, ok most welcome.
1.First you need to open Command Promote (CMD).Click Start Button and type CMD and open it with Administration.
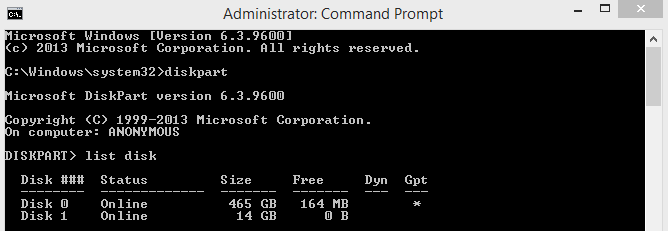
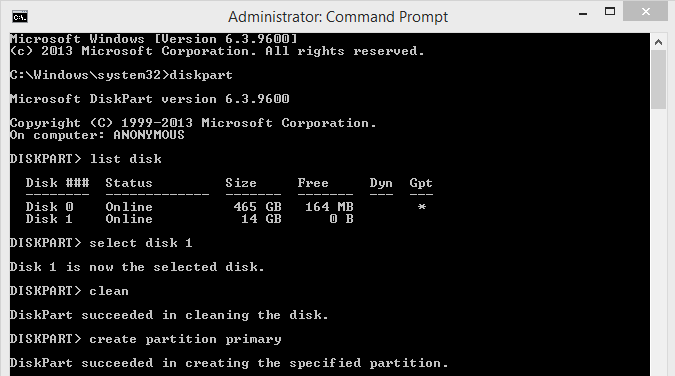
2.Type diskpart
3.Then Type "list Disk"
It will show Disk list..Such as first or Disk 0 is showing Your hard drive then next all off showing external hard drive (such as pen drive )
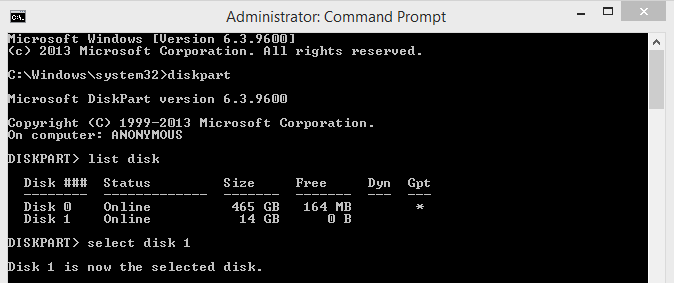
4. Then which drive i want to boot able.Now i want to show Disk 1. Because Disk 1 is my pen drive. So let Start
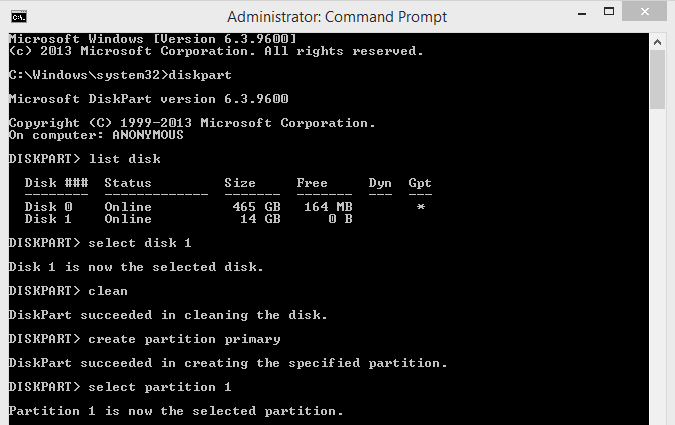
Type "select disk 1"
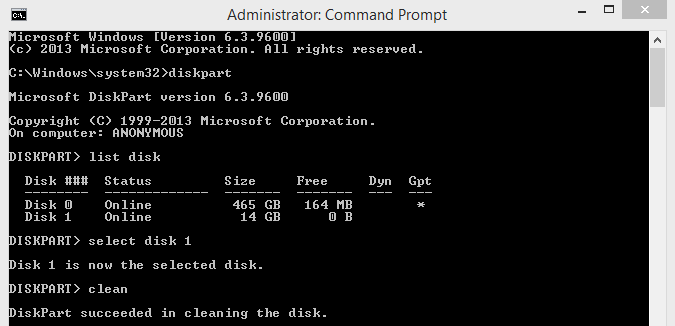
5. You need to clean your Disk-part. So type "clean"
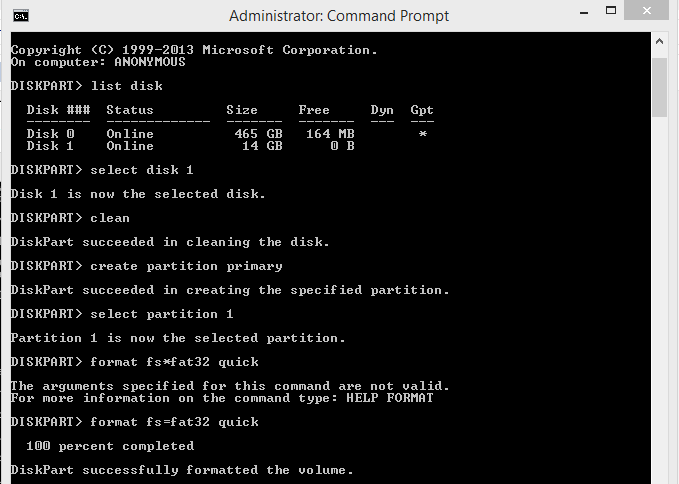
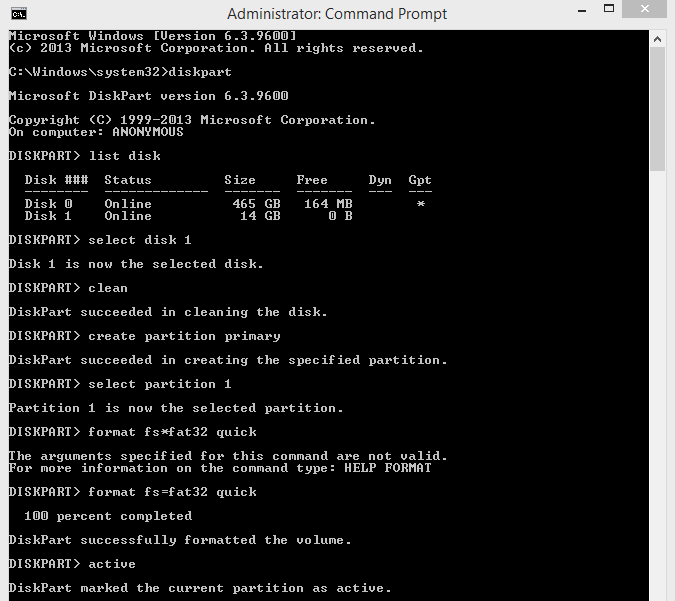
6. Now you need to create partition. So type "create partition primary"
Now Let's Enjoy !!!!!!!!!!!!!!
Make Bootable USB pendrive for ALL Windows || Cyber Security Blog
Subscribe to:
Posts (Atom)